Enterprise-Grade Security Testing at Machine Speed
AI-powered penetration testing that delivers comprehensive vulnerability assessments in hours, not weeks.
Start a PentestTrusted by Security Teams
Real vulnerabilities.Validated and reproducible.
Your AI security force multiplier
Deploy autonomous AI agents that work in parallel to discover, validate, and exploit vulnerabilities across your entire attack surface—without human intervention
Autonomous AI Agents
AI-powered agents trained on extensive attack patterns execute comprehensive penetration testing across web applications, APIs, and infrastructure at machine speed.
On-demand Pentesting
Launch security assessments in hours, not weeks. Seamlessly integrate into CI/CD pipelines for continuous security validation throughout your development cycle.
Complete Attack Surface Coverage
Systematic testing of every endpoint, parameter, and authentication mechanism ensures comprehensive coverage with zero blind spots.
Proven Results
Validated against real-world vulnerabilities with 500+ application vulnerabilities discovered since September 2025, delivering reproducible proof-of-concepts.
AI-powered vulnerability identification and exploitation
Autonomous AI agents that identify, validate, and exploit vulnerabilities across your entire application stack
Intelligent Vulnerability Discovery
Our AI pentesting solution automatically identifies vulnerabilities across web applications, APIs, and infrastructure. Advanced algorithms detect security flaws including SQL injection, XSS, authentication bypasses, and more.
Automated Exploitation
AI agents not only identify vulnerabilities but also exploit them safely to demonstrate impact. Generate proof-of-concept exploits that validate security issues and provide actionable remediation guidance.
Comprehensive Vulnerability Coverage
Systematically test every endpoint, parameter, and attack vector. Our AI solution identifies vulnerabilities across OWASP Top 10, authentication mechanisms, authorization flaws, and business logic vulnerabilities.
Real-time Security Assessment
Continuous AI-powered scanning identifies and exploits vulnerabilities as they emerge. Integrate into your development workflow for real-time security validation with detailed exploit reports and remediation steps.
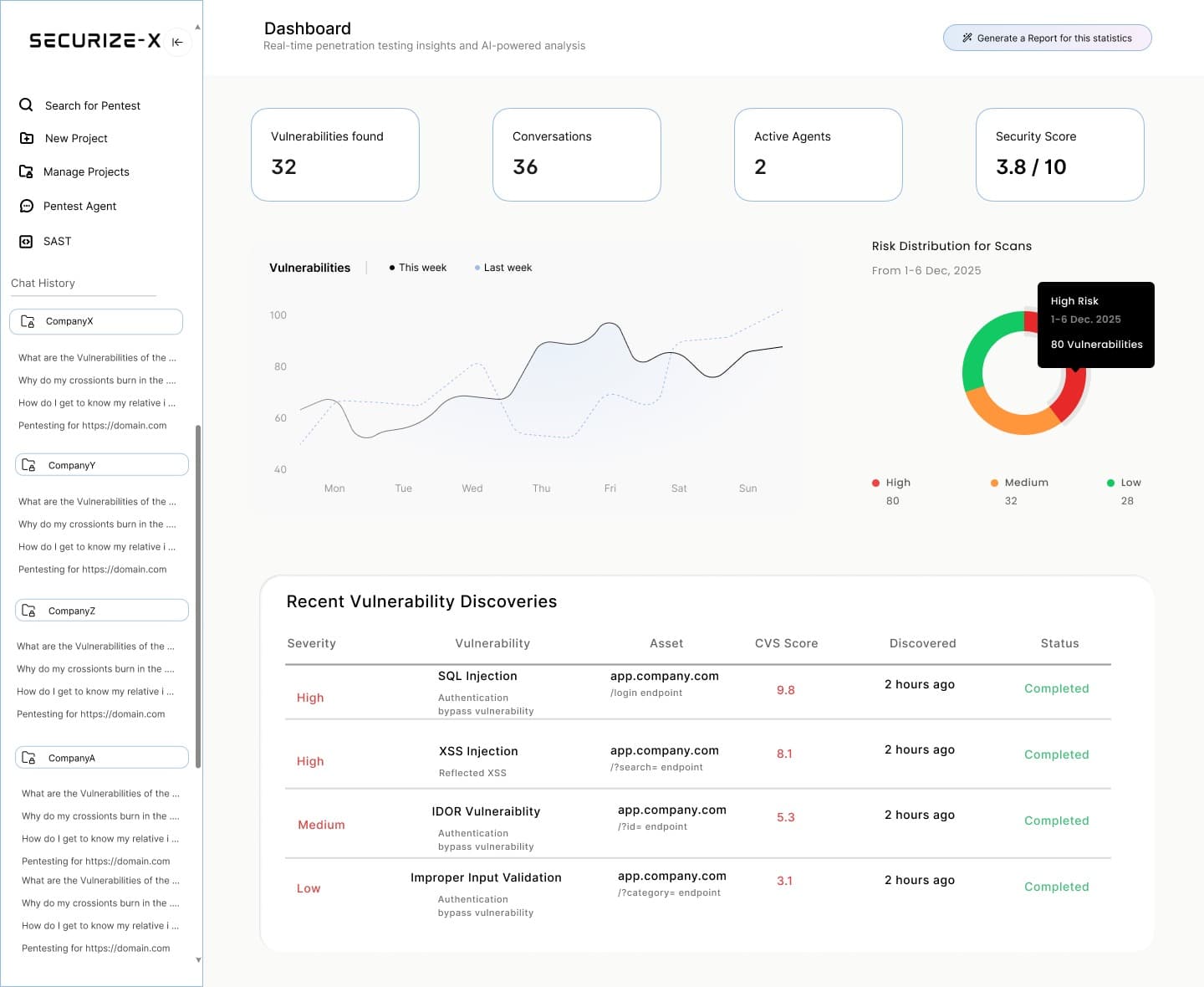
Watch Securize hunt forvulnerabilities in yourapplications
Experience real-time penetration testing insights and AI-powered analysis through our comprehensive security dashboard.
Get a Demo